
Cyber Security Services
Protecting Your Digital Assets with Confidence
In an era where cyber threats are increasingly sophisticated, businesses must prioritize the security of their digital environments. At Dreamworth Solutions, we are more than just a cyber security provider; we are your trusted partner in safeguarding your assets, ensuring compliance, and empowering you to operate confidently in the digital landscape.
Understanding Cyber Security
Cyber security encompasses the technologies, processes, and practices designed to protect networks, devices, programs, and data from attack, damage, or unauthorized access. It involves a wide range of measures that businesses can implement to safeguard their information systems from cyber threats, which can result in financial loss, reputational damage, and legal consequences.
The significance of cyber security cannot be overstated, especially as cyber threats become more sophisticated and prevalent. Organizations of all sizes must prioritize their cyber security strategies to mitigate risks effectively.
When Should You Consider Cyber Security Services?
Engaging cyber security services is crucial when:
- Launching New Systems or Applications: New technology can introduce vulnerabilities that need immediate attention.
- Experiencing Data Breaches: If you’ve suffered a breach, it’s vital to assess and enhance your security measures.
- Compliance Requirements: Regulatory mandates necessitate a robust security posture to protect sensitive data.
- Digital Transformation Initiatives: As you embrace digital solutions, ensure your security framework evolves accordingly.
Who Needs Cyber Security Services?
Every organization, regardless of size or industry, can benefit from cyber security services. Whether you are a startup, a mid-sized enterprise, or a large corporation, safeguarding your data and systems is essential for maintaining trust and operational integrity.
Industry Trends and Competitor Actions
As cyber threats evolve, businesses must adopt a proactive stance. Many organizations are shifting from reactive measures to comprehensive, multi-layered security strategies. While competitors may offer basic security solutions, Dreamworth Solutions stands out with our tailored, end-to-end cyber security services designed to address both current and emerging threats.
Why Choose Dreamworth Solutions?
At Dreamworth Solutions, we are committed to providing cutting-edge cyber security solutions that combine technical expertise with strategic insight. Our key differentiators include:
- Comprehensive Security Assessment: We conduct thorough evaluations to identify vulnerabilities and recommend tailored solutions.
- Proactive Threat Management: Our advanced monitoring and response capabilities ensure threats are neutralized before they impact your business.
- Expert Team: Our team consists of industry-certified professionals with extensive experience in various sectors.
- Custom Solutions: We understand that no two businesses are alike; our services are tailored to fit your specific needs.
- Ongoing Support and Training: We don’t just implement solutions; we empower your team with the knowledge and tools needed to maintain security.
Our Cyber Security Services
In addition to our core offerings, Dreamworth Solutions provides specialized services tailored to meet the demands of modern businesses. Here’s a brief overview of our offerings:

Cloud Security
Our Cloud security services offer threat detection, data encryption, identity and access management, and security monitoring for cloud-based assets. These services protect cloud environments from unauthorized access, data breaches, and cyber threats.
VIEW DETAILS VIEW DETAILS
Infrastructure Security
Our Infrastructure security services include protecting physical and virtual systems through network security, firewalls, intrusion detection systems, and vulnerability assessments. These services ensure the integrity, availability, and confidentiality of an organization's infrastructure.
VIEW DETAILS VIEW DETAILS
Vulnerability / Penetration Testing
Our services under Vulnerability and penetration testing includes identify security weaknesses by simulating real-world attacks, assessing systems, networks, and applications for vulnerabilities. These services help organizations strengthen their defenses by providing detailed reports and remediation guidance.
VIEW DETAILS VIEW DETAILS
Compliance Assessment
Our Compliance assessment services evaluate an organization's adherence to regulatory standards like GDPR, HIPAA, or PCI-DSS, ensuring legal and security obligations are met. These services include audits, gap analyses, and guidance on achieving compliance.
Dreamworth Solutions: Lifecycle of Cyber Security Implementation
At Dreamworth Solutions, our approach to cyber security is structured around a comprehensive lifecycle, ensuring that every aspect of your security needs is addressed methodically. This multi-stage process guarantees robust protection and ongoing support.
Lifecycle of Cyber Security Implementation at Dreamworth Solutions
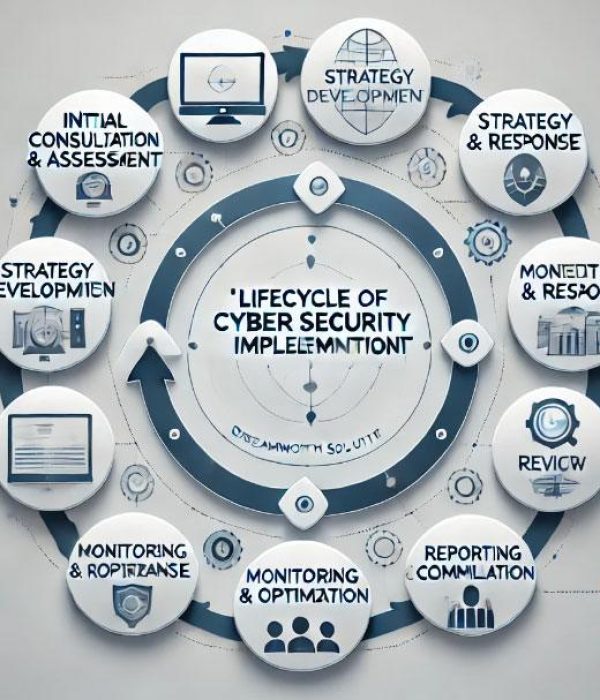
- Initial Consultation & Assessment
- Understanding Your Needs: We begin with a detailed consultation to understand your unique security requirements and business objectives.
- Vulnerability Assessment: Conducting a thorough analysis to identify potential weaknesses in your systems.
- Strategy Development
- Risk Management Planning: Creating a customized security strategy based on your specific risks and compliance needs.
- Technology Selection: Recommending the right technologies and tools to implement your security strategy effectively.
- Implementation
- Deployment: Implementing security solutions, including software, hardware, and processes, to safeguard your systems.
- Training: Providing necessary training to your staff to ensure they are aware of security protocols and best practices.
- Monitoring and Response
- Real-Time Monitoring: Utilizing advanced tools to monitor your systems continuously for potential threats.
- Incident Response: Establishing a clear plan for responding to security incidents quickly and efficiently.
- Review and Optimization
- Ongoing Assessment: Regularly reviewing security measures to identify areas for improvement.
- Updating Protocols: Ensuring your security measures evolve with emerging threats and changes in your business.
- Reporting and Compliance
- Detailed Reporting: Providing regular reports on security status, incidents, and compliance efforts.
- Audit Support: Assisting with compliance audits and assessments as required.
Case Study: How Dreamworth Solutions Secured Client Y
Client Overview: A mid-sized financial services firm facing increasing cyber threats and regulatory scrutiny.
Objective: To develop a robust cyber security framework that ensured compliance and protected sensitive financial data.
Step 1: Initial Consultation:We engaged with the client to understand their specific security challenges and compliance requirements.
Step 2: Risk Assessment:A comprehensive risk assessment identified multiple vulnerabilities in their systems, prompting the need for immediate action.
Step 3: Strategy Development:We designed a tailored security strategy that included network security enhancements, endpoint protection, and employee training programs.
Step 4: Implementation:Our team implemented the necessary security measures, conducted training sessions, and established monitoring protocols.
Step 5: Results
- Enhanced Security Posture: Achieved a significant reduction in security incidents.
- Compliance: Successfully met regulatory requirements, ensuring peace of mind for the client.
- Increased Confidence: The client reported improved trust from their customers due to their enhanced security measures.
Dreamworth Solutions is your trusted partner in navigating the complex landscape of cyber security. Our commitment to innovation, thoroughness, and customer satisfaction sets us apart. With our proven track record, we ensure your organization remains secure and compliant, allowing you to focus on growth.
If you’re looking for a cyber security partner that prioritizes your safety and success, Dreamworth Solutions is here for you. Contact us today to discover how we can fortify your digital assets and build a secure future together.
