Web Application Penetration Testing
Increased cyber attacks and software risks have reinforced security experts to dig deeper into the security framework and to come out with powerful security solutions to sustain in the worst situation. However, preventive solutions are always better and preferred than remedial measures. One of the great security solutions is penetration testing. A penetration test is also termed as a pen test, is a kind of simulated cyber attack against your IT system to assess for exploitable vulnerabilities.

Pen test works by the purposeful breaching of multiple numbers of application systems like application protocol interfaces (APIs) or frontend/backend servers to detect vulnerabilities.
The requirement of Penetration testing
As we discussed in the previous section, security IT systems and infrastructure is paramount for all organizations, the penetration testing approach was devised to strengthen the security framework. Before going into its further details, we should be clear about the concept of vulnerability. The vulnerability is a term used to refer to flaws or defects in the system which can render the system to security weaknesses and threats.
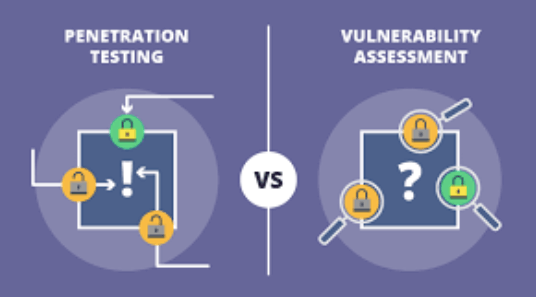
A Quick Comparison – Vulnerability Scanning and Pen Testing
Vulnerability Scanning is intended to find out the known weaknesses or flaws in the application and provide methods to fix and enhance the complete security of the application. It focuses on various tasks like installation of security patches, adequate configurations, etc.
On the other hand, Pen Tests simulates real-time systems and mainly provides insights on unauthorized user access to the system, possible damage, and a data portion that is damaged, etc.
- Need for Web App Penetration Testing
- Pen tests provides a way to find unknown vulnerabilities.
- Overall assessment of security policies.
- Proper testing of the components like routers, firewalls, and DNS.
- Finding vulnerable attack paths that can hamper the web application.
- Finding loopholes that can affect sensitive data.
Increased use of smartphones has increased the possibility of cyber-attacks and compromising of data. Penetration Testing is an important tool in ensuring the formation of a security system that can be employed by users without any issues of hacking or data loss.
Web Penetration Testing Methodology
Web Penetration Testing Methodology offers a set of security industry guidelines and standards on how penetration testing should be performed. There are well-defined methodologies and standards which can be applied for testing but depending on the demands of each web application, testers can use their methods of penetration testing.
Popular Security Testing Methodologies and standards include –
OWASP (Open Web Application Security Project)
PCI DSS (Payment Card Industry Data Security Standard)
PTF (Penetration Testing Framework)
OSSTMM (Open Source Security Testing Methodology Manual)
ISSAF (Information Systems Security Assessment Framework)
Test Scenarios for Web Application Pen Test
Following is the list of some of the test scenarios where web application pen test can be performed.
Cross-Site Scripting
Session management
Cross-Site Request Forgery
SQL Injection
Caching Server Attacks
Broken authentication
File Upload flaws
Security Misconfigurations
Types of Web Penetration Testing
Web penetration testing can be categorized in two ways based on inside or outside attacks.
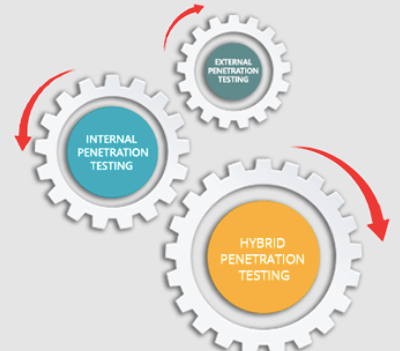
Internal Penetration Testing
As its name implies, the internal penetration testing is associated with the single organization and hence, it includes testing web applications hosted on the intranet through LAN. It also finds any existing vulnerabilities within the corporate firewall.
However, security experts mainly assume that attacks happen externally, and hence, internal pen test becomes less significant from a security perspective. But these tests can be advantageous to avoid malicious employee attacks or ex-employee attacks on your web systems. It also prevents your web applications from phishing attacks, social engineering attacks, misuse of user privileges, and unlocked terminals.
External Penetration Testing
External penetration testing handles security threats that arise from outside the organization and it includes testing web applications that are hosted on the internet. Here, testers have to behave like a hacker with no detailed knowledge of the internal system. Testers are provided with the IP of the target system and they are not equipped with any other information. Thereafter, testers search and scan public web pages and get information about target hosts. Alongside it also tests firewalls, servers, and IDS.
Blind testing
In a blind test approach, a tester is only provided the name of the organization that’s being targeted. This approach is beneficial as it offers security personnel a real-time outlook of how an actual application attack would occur.
Double-blind testing
In a double-blind test approach of web application penetration testing, security personnel lack the knowledge of the planned simulated attack. This approach won’t provide any time to manage defences before an attempted breach.
Targeted testing
In this pen test approach, both the tester and security personnel work jointly and appraise each other for their movements. This is a significant training practice that offers security personnel with real-time feedback from an attacker’s point of view.
Pen Test Framework
Planning Phase- Before Testing
The planning phase for the web app penetration testing involves the following subtasks.
Scope – Here the scope for testing activity is defined and it is performed before actual testing activity.
Documentation availability – At this stage testers are provided with all important documents like web architecture, web services integration, integration points, etc. The testers are also informed about HTTP/HTTPS protocol fundamentals, Web Application Architecture, and traffic interception ways.
Success Criteria Determination – For web application pen testing success criteria is well defined and approved.
Review of test results – It is a best practice to review prior test results for understanding what vulnerabilities existed in the past and what type of remediation was taken to handle them. This approach offers a better clarification to the testers.
Understanding the environment – Testers should acquire knowledge regarding the associated environment before executing pen-testing. During this step, testers sharpen their knowledge of firewalls or security protocols that needs to be disabled to undertake the testing activity.
Pen Test Execution Phase – During Testing
Web Penetration testing is performed at this stage and that too from any location provided if any other port restrictions are not imposed.
Running tests with various user roles – Testers should continue to execute tests with various user role accounts since the system may react varyingly to users defined with different privileges.
Handling of Post-Exploitation – Testers must employ the predefined Success Criteria defined in the previous step to report and tackle any exploitation; also, it is expected that they should follow the defined path to deal with vulnerabilities. This step is aimed to find out what needs to be executed after testers have noticed that the system has been attacked.
Test Reports Generation – Any Testing activity performed without proper reporting doesn’t help the enterprise much and penetration testing of web applications is not an exception. At this stage testers should ensure the test results are properly circulated with all stakeholders by creating proper reports with insights on vulnerabilities observed, the methodology applied for testing, severity and the location of the issue noticed.
Post Execution Phase of Pen Test – After Testing
The final step covers the following activities.
Suggest remediation – Pen Testing is not just the final step for finding vulnerabilities. The associated security team including a QA member should study the outcomes reported by Testers and then place the appropriate remediation.
Retest Vulnerabilities – After the remediation is suggested and implemented, testers should perform retests to confirm that the fixed vulnerabilities would not reappear.
Clean up – As part of the Pen test, testers make many changes like the proxy settings changes, configuration changes, so at the end, clean up should be done and all changes are restored.
Services & Solutions by Dreamworth
Being an excellent partner for web services, Dreamworth Solutions provides quality web application pen test and vulnerability assessment services to its global clients. Our 10 years of flourishing and enriching experience of web services makes us the top choice of many companies as their security partner for IT infrastructure. Take a look at our web application penetration service model that distinguishes us from all contemporaries.
Scope definition and Threat Modelling
We consider your security requirements and accordingly, model the right security framework to serve your requirements.
Use of Automated Testing Tools
The use of advanced security testing tools helps us to reach the number of possible vulnerabilities within your web application and IT infrastructure.

Manual Penetration Testing
We not only rely on automated test results, but our security testers also explore vulnerabilities noticed through results from automated tools and other reported threats as per the personalized test plan.
Speedy Vulnerability Reporting
We provide insights on all emergency and critical vulnerabilities to our clients immediately so that their development team can proceed further to resolve them.
Detailed Test Reports
Our professionally created detailed reports contain best-practice resolutions for each noticed vulnerability along with other significant factors.
Validation of Vulnerability Resolution
Retests activities help us to validate that your development team has resolved the reported vulnerabilities and other threats.
Bottomline
IT security requirements get connected with Dreamworth Solutions. Just share your requirements to our business team and be assured that your IT assets are in safe hands now. We provide customized packages to our clients, with no other imposed conditions and hence, we are the top choice of many firms for their IT infrastructure security requirements. Share your business requirements and be a part of Dreamworth Solutions’ huge proud consumer base.
We’re excited to hear from you and let’s start something
